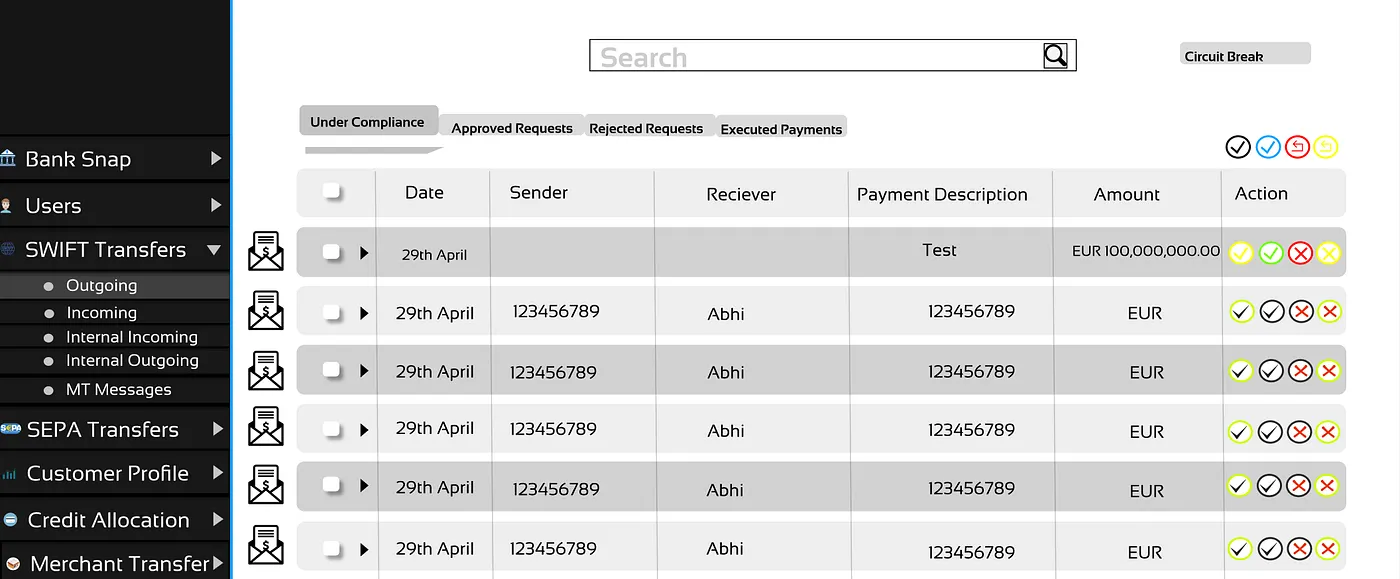
Banking Cloud Admin Dashboard with SWIFT Transfers management interface
International banking infrastructure remains one of the least documented domains in technology. This article shares insights from building end-to-end infrastructure for banks, including international banking licenses, corporate banking policies, and IT frameworks that address critical bottlenecks in global money movement.
The Core Problem: Legacy Infrastructure Meets Modern Requirements
SWIFT (Society for Worldwide Interbank Financial Telecommunication) handles the majority of international transactions. However, the traditional cloud offerings available through SWIFT are constrained by dated technology and security gaps that create real operational risks.
The challenge: how do you build a customized infrastructure solution for SWIFT messaging that provides cloud benefits (scalability, accessibility, automation) while maintaining the security integrity that banking demands?
The answer lies in understanding that you cannot simply "cloudify" banking infrastructure. Instead, you must design a hybrid architecture where the cloud handles virtual state management and administration, while real transactions flow through secured offline infrastructure.
Understanding SWIFT Autoclient
For those unfamiliar with banking infrastructure, Autoclient is a system that connects with the SWIFT network to send messages among banks worldwide about transactions. The conventional system requires an encrypted USB key for access and provides automation for sending FIN formatted files containing MT format messages to other banks and network institutions.
The MT103 message type format is the most common message type for sending transactions through SWIFT. The Autoclient system allows bulk clearing of FIN formatted files, enabling multiple transactions (messages) to process simultaneously.
MT103 Message Structure
MT103 messages contain structured fields for sender and receiver bank identification (BIC codes), transaction amounts, currency codes, value dates, ordering customer details, beneficiary information, and remittance details. Each field has specific formatting requirements that must be precisely followed for the message to be accepted by the SWIFT network.
The Security Architecture
An average bank faces a major hacking attempt every six hours. Connecting to cloud infrastructure without a defensible architecture is not viable. The Bangladesh Central Bank hack demonstrated what happens when security gaps are exploited, but most banking security incidents never receive media attention due to legal and reputational concerns.
The solution requires multiple layers of security:
Bi-Layered Ledger System
Administration is conducted across two different servers hosted through VPNs in an Oracle DB on the local server. An image is placed on every interaction, with codebase replication at standardized intervals (typically 5 minutes). Switch ports defend against attacks through custom scanners that analyse out-of-ordinary ledger changes or code changes and revert to a previous state on a different server.
Data Pipeline Security
Multiple data pipelines with double encryption and complete tokenization of all data. The system never directly connects to the local server. Instead, manual wiring switchboards the virtual state with live SWIFT infrastructure. When a new state reflects through the pipelines, it passes through decryption and state check, then switches through from local hardware in two different locations.
A middleware check from a cloud state matches the two states before funneling through to the SWIFT server. This creates an effective offline cloud system where real transactions are based in an offline data warehouse in a secure vault, while cloud-based functionality handles only the virtual system.
Outgoing Transaction Flow
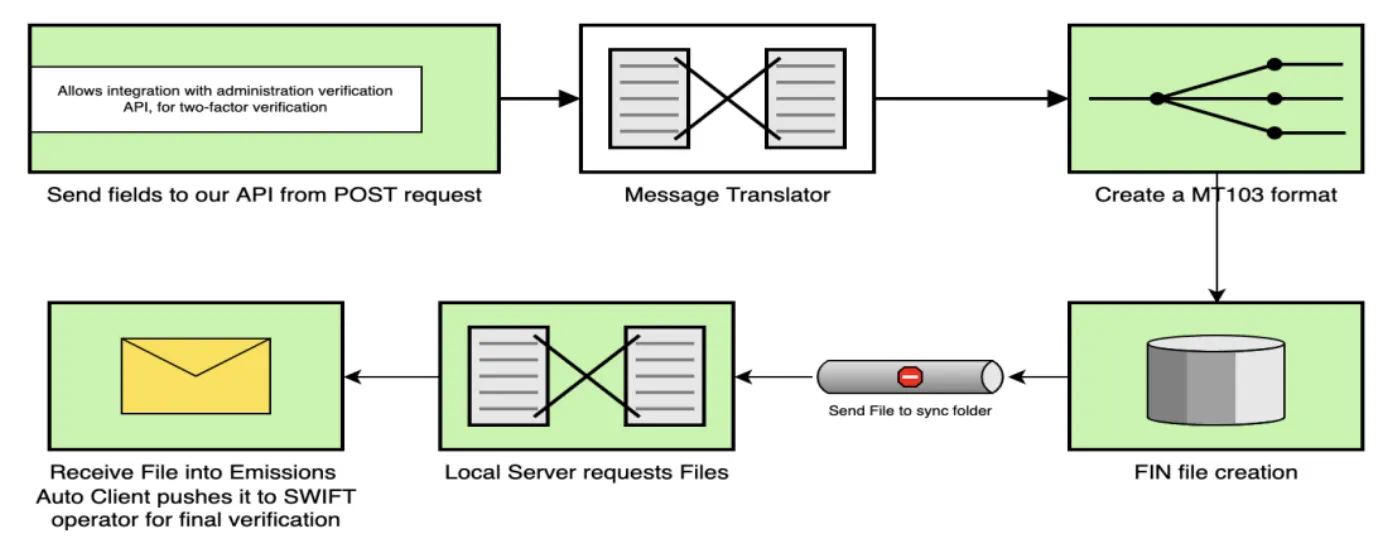
MT Outgoing Message Flow: From API POST request to SWIFT operator verification
The system syncs with SWIFT's Autoclient emissions folder and receives FIN files formatted to MT requirements from fields provided by the client through the front-end. For security, Linux-based systems (preferably hardened distributions) are used rather than Windows due to the ability to close obvious security loopholes.
For cloud deployment, an S3 bucket stores all FIN formatted files waiting to be synced after a set timer. Sequenced decryptions and double layering protect each transmission. To send requests, an API request with a unique ID posts to the API gateway, which automatically processes the request and sends the FIN file to the Autoclient system.
The file is archived and appears in the operator system for verification. Bipartite verification can be configured: one in the admin panel of the web platform, another in the SWIFT system for operator verification. This architecture handles millions of activity nodes simultaneously.
Incoming Transaction Flow
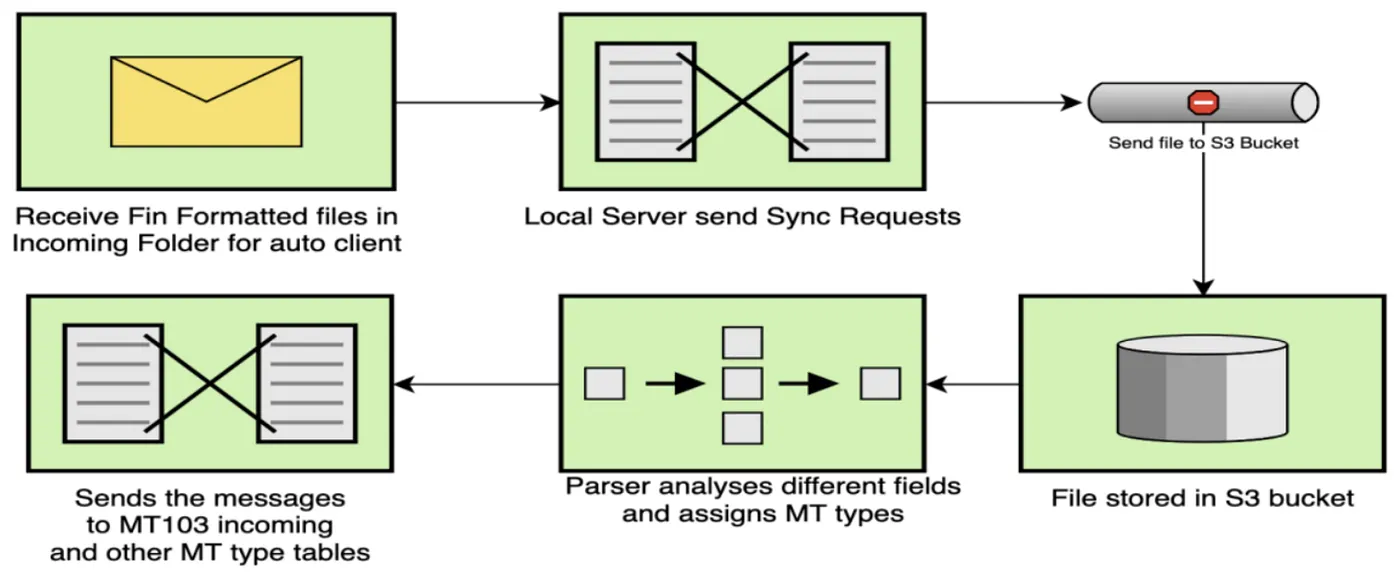
MT Incoming Message Flow: From Autoclient folder to parsed MT type tables
Incoming folders sync with the S3 bucket where FIN files are pushed. A parser reads the various message types and places them in correct fields for display in two incoming tables: one for MT103 transactions and another for all other message types.
The API triggers pending, approval, and rejection mechanisms and integrates with balance triggers for transaction histories and balance creation. Setting up the sync and relevant software on the local server enables automatic file synchronization with data flowing directly to queryable database tables.
Scaling Considerations
For high-frequency and ML-heavy tasks, fast data pipelines like Kafka and Spark with Aerospike as the database provide the necessary performance. This architecture becomes infinitely scalable when load balancing is done correctly with partitions allocated in a set framework.
The system can extend beyond SWIFT to integrate with regional systems like SEPA, creating a unified administration layer across multiple transaction networks while maintaining the security properties required for each.
First Principles of Banking Infrastructure
- →Never directly connect cloud to production banking systems
- →Assume every system will be attacked; design for recovery, not just prevention
- →Multiple verification layers are mandatory, not optional
- →The cloud handles administration; real value flows through secured offline infrastructure
- →Blend multiple technologies and languages to avoid single-vector vulnerabilities
Implications for Modern Banking
Building banking infrastructure is not about choosing between cloud convenience and traditional security. It's about understanding that these systems handle real value representing people's savings, business operations, and economic activity.
The approach outlined here provides a framework for banks that want modern infrastructure without compromising on the security that the industry demands. It requires significant expertise to implement correctly, but the result is infrastructure that serves both operational efficiency and regulatory requirements.
The documentation gap in banking technology is significant. Many institutions rely on expensive legacy systems not because they are better, but because the knowledge required to build alternatives is not readily available. Closing this knowledge gap is essential for the industry to evolve.